We’ve been there. You’re managing servers, juggling passwords, trying to remember which credential goes where, and somewhere in the back of your mind, you know this isn’t how things should work. Passwords are annoying at best and a security nightmare at worst. So yeah, we built something better.
SSH public key management just landed in KloudBean, and honestly, it’s one of those features that feels like it should’ve existed from day one. But here’s the thing – we wanted to get it right. Not just functional, but actually usable. Because what’s the point of a security feature if it’s so complicated that nobody wants to use it?
The Password Problem Nobody Talks About
Let’s be real for a second. How many times have you reset a server password because you forgot it? Or worse, kept using the same password across multiple servers because it’s just easier to remember? We’ve all done it. I’ve done it. It’s terrible for security, but when you’re in the middle of debugging at 2 AM, convenience wins.
Then there’s the team access problem. Someone new joins your team, and suddenly you’re sharing credentials over Slack (please tell me it’s at least Slack and not email). Someone leaves, and now you’ve got to change all the passwords and redistribute them. It’s exhausting and frankly a bit ridiculous in 2025.
SSH keys solve this, but let’s be honest – they’ve always felt like something only hardcore sysadmins bothered with. The command line stuff, the key generation, the manual copying of keys to servers… it works, but it’s not exactly welcoming. We wanted to change that.
What We Actually Built
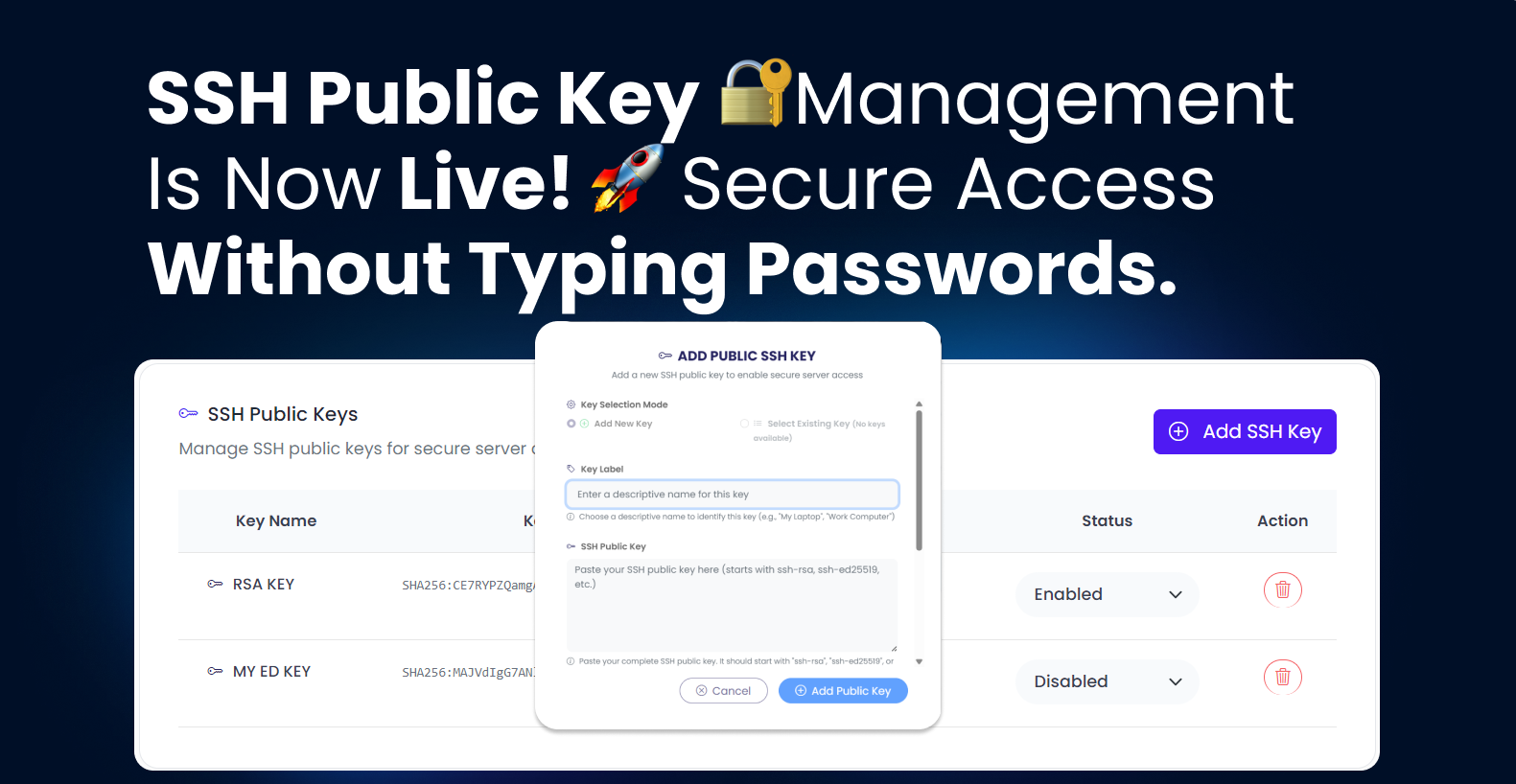
The new SSH key management feature in KloudBean lets you add, manage, and revoke SSH public keys directly from your dashboard. No terminal gymnastics required, though you’re obviously welcome to do things the old-school way if that’s your thing.
Here’s what it looks like in practice. You’ve got a server running on KloudBean. You want to access it securely without passwords. You click “Add Public SSH Key,” give it a label like “My MacBook” or “Work Laptop” (because trust me, you’ll forget which key is which otherwise), paste your public key, and boom – you’re done. Next time you SSH into that server, it just works. No password prompt, no friction, just access.
The modal we built guides you through the whole thing. We added helper text that actually helps instead of just being there for decoration. It tells you exactly what format the key should be in, gives you examples, and if something’s wrong, the error messages are clear enough that you don’t need to Google them.
Why This Matters More Than You Think
Security features have this reputation for being complicated, and I think that’s why a lot of people skip them. But SSH keys aren’t just about security – they’re about making your life easier. Once you set them up, you never have to type a password again for that server. It’s faster, it’s more convenient, and it happens to be way more secure. Win-win-win.
For teams, this changes everything. Each person generates their own key pair and adds their public key to the server. When someone leaves or loses their laptop, you just remove their key. You don’t have to coordinate password changes with the entire team. You don’t have to worry about old credentials floating around somewhere.
We’ve also thought about the edge cases that usually trip people up. What if you want to temporarily disable someone’s access without removing their key entirely? There’s a toggle for that. What if you need to add multiple keys from different devices? Go ahead, add as many as you want. Each one gets its own label so you can keep track of what’s what.
The Technical Stuff (For Those Who Care)
Under the hood, we’re following standard SSH protocol conventions. Your public keys are stored securely on your server’s authorized_keys file, exactly where they should be. We support RSA, Ed25519, and other modern key types. The minimum recommended key length is 2048 bits, though we’d suggest going with 4096 for RSA or just using Ed25519 because it’s faster and arguably more secure.
When you add a key, we validate it immediately. Not just “does this look like a key” validation, but actual cryptographic validation to make sure it’s properly formatted and actually usable. We’ve all copy-pasted things wrong before – better to catch it now than when you’re locked out of your server.
The interface also shows you exactly what command to use for connecting to your server. It’s right there in the dashboard with a copy button because why should you have to memorize or reconstruct SSH commands? We’re building tools to make your life easier, not to test your memory.
How Real Teams Are Already Using This
We’ve had a few teams testing this feature before the public release, and the feedback has been interesting. One team told us they used to have a shared “deploy” user with a password they’d change monthly. They’d set calendar reminders, update their CI/CD configs, notify everyone, and inevitably someone would miss the memo and deployments would break. Now each team member has their own key, and their deployment pipelines have dedicated keys. No more monthly password rotation dance.
Another user mentioned they travel a lot for work and switch between their laptop, desktop, and sometimes a tablet. They added keys for all three devices with labels like “MacBook Pro,” “Home Desktop,” and “iPad Emergency Access.” Now they can manage their servers from wherever without dealing with password managers or security concerns.
The CI/CD use case is particularly interesting. You can generate a key specifically for your GitHub Actions or deployment pipeline, add it to your KloudBean server, and never worry about credentials in your code repository. When you eventually migrate to a different CI/CD platform or rotate credentials, you just swap out that one key. Everything else keeps working.
What We’re Not Doing (And Why That’s Good)
We deliberately didn’t build some features that might seem obvious. We’re not managing your private keys. Those live on your computer, and they should stay there. The moment a platform starts “managing” private keys is the moment you should probably find a different platform.
We’re also not generating keys for you. Yes, we could add a “Generate Key Pair” button, but then we’d have to transmit your private key over the network to your computer, even briefly. That’s a terrible idea. Your private key should be generated on your machine and never leave it. We provide clear documentation on how to generate keys locally, but we’re not going to make it easier at the cost of security.
There’s no key recovery feature either. If you lose your private key, that’s it – you’ll need to generate a new one. This sounds harsh, but it’s actually how SSH keys are supposed to work. They’re not passwords you can reset. The whole security model depends on private keys staying private and being unrecoverable if lost.
The Little Details That Add Up
We added an empty state for when you haven’t added any keys yet. It’s not just a blank page with an “Add” button – it actually explains what SSH keys are and why you might want to use them. Because not everyone managing servers is a DevOps expert, and that’s totally fine.
The key label field has placeholder text with actual examples instead of generic “Enter label here” text. Small thing, but it makes a difference when you’re setting up your first key and wondering what to name it.
There’s a “Keep Enabled” toggle on each key. This is for situations where you want to temporarily disable access without deleting the key entirely. Maybe someone’s on vacation, or you’re troubleshooting and want to narrow down which key is causing an issue. You can flip it off, check what you need to check, and flip it back on.
The modal form validates as you type. You don’t have to fill everything out and click submit only to find out your key format was wrong. It tells you immediately, right there, with a clear explanation of what’s expected.
What’s Next
This is version one. It works, it’s solid, and we’re proud of it. But we’re already thinking about what comes next. Key expiration dates would be useful for temporary contractor access. Key usage analytics could show you which keys are actually being used and which are just sitting there. Team-level key management where organization admins can see and manage all keys across all servers.
We’re also considering SSH certificate support for larger teams, though that’s a bit further down the roadmap. The current key-based system works great for most use cases, but certificates offer some interesting benefits for enterprise scenarios.
For now though, we’re focused on making sure this release is rock solid. We’ve fixed the bugs we found during testing, polished the interface until it felt right, and we’re ready to see how you all use it.
Just Ship It Already
So yeah, SSH public key management is live in KloudBean. If you’ve been putting off switching from passwords, now’s a good time. If you’ve been manually managing SSH keys and wishing there was a better way, well, here’s a better way.
Go add some keys. Label them properly. And enjoy never typing a server password again. You can thank us later, probably when you’re effortlessly SSH-ing into your server at 2 AM without fumbling for credentials.
The feature’s available now for all KloudBean users. No extra cost, no premium tier required – it’s just part of the platform. Because security features shouldn’t be paywalled. They should be default.
Check out the documentation if you need help getting started, or just dive in and click around. We built it to be intuitive enough that you probably won’t need the docs anyway. But they’re there if you want them, complete with examples and troubleshooting tips.
Now go forth and manage those keys. Your future self will thank you.